CVE-2022-23648 – Arbitrary Host File Access from Containers Launched by Containerd CRI and its Impact on Kubernetes
Published 04/06/2022
 This blog was originally published by ARMO here.
This blog was originally published by ARMO here.
Written by Leonid Sandler, CTO & Co-founder, ARMO.
Recently discovered vulnerability - CVE-2022-23648 - in containerd, a popular container runtime, allows especially containers to gain read-only access to files from the host machine. While general container isolation is expected to prevent such access, in Kubernetes, it is especially dangerous because well-known and highly sensitive files are stored in known locations on the host.
Impact on Kubernetes
The most attractive file for the attackers to target will be the kubelet’s private key, used to communicate between node kubelet and the KubeAPI server. Kubelet is an absolutely trusted component in Kubernetes, and it can ask the KubeAPI server to provide any information stored in ETCD, such as Kubernetes Secrets, ConfigMaps, etc. This information can be exfiltrated or used locally to access protected interfaces and data assets in the Kubernetes and even the entire cloud infrastructure.
Is your cluster vulnerable?
If you are running containerd versions prior to 1.6.1, 1.5.10, and 1.14.12, your cluster is susceptible to potential attacks utilizing this vulnerability.
Kubescape has developed a dedicated control - C-0087 – under the ArmoBest framework, verifying if containerd is the active CRI and checking vulnerable version numbers.
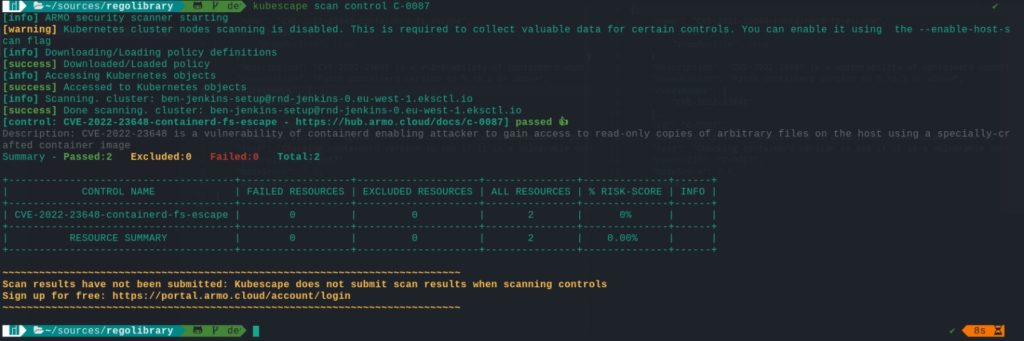 Kubesxape C-0087
Kubesxape C-0087Mitigation and verification
If your cluster is vulnerable, it’s highly recommended to upgrade the containerd version as soon as possible.
In the meantime, make sure that all your deployment definitions come from a trusted source and do not attempt to specify a volume referencing a suspicious path on the host machine.
Please install or update to the latest Kubescape version from GitHub or via the following command:
curl -s https://raw.githubusercontent.com/armosec/kubescape/master/install.sh | /bin/bash
To scan your cluster use the following command:
kubescape scan framework armobest
Unlock Cloud Security Insights
Subscribe to our newsletter for the latest expert trends and updates
Related Articles:
Agentic AI Pen Testing: Speed at Scale, Certainty with Humans
Published: 01/26/2026
My Top 10 Predictions for Agentic AI in 2026
Published: 01/16/2026
Best Practices to Achieve the Benefits of Agentic AI in Pentesting
Published: 01/13/2026
Microsoft Entra ID Vulnerability: The Discovery That Shook Identity Security
Published: 12/08/2025



.jpeg)


.jpeg)